Threat Investigator
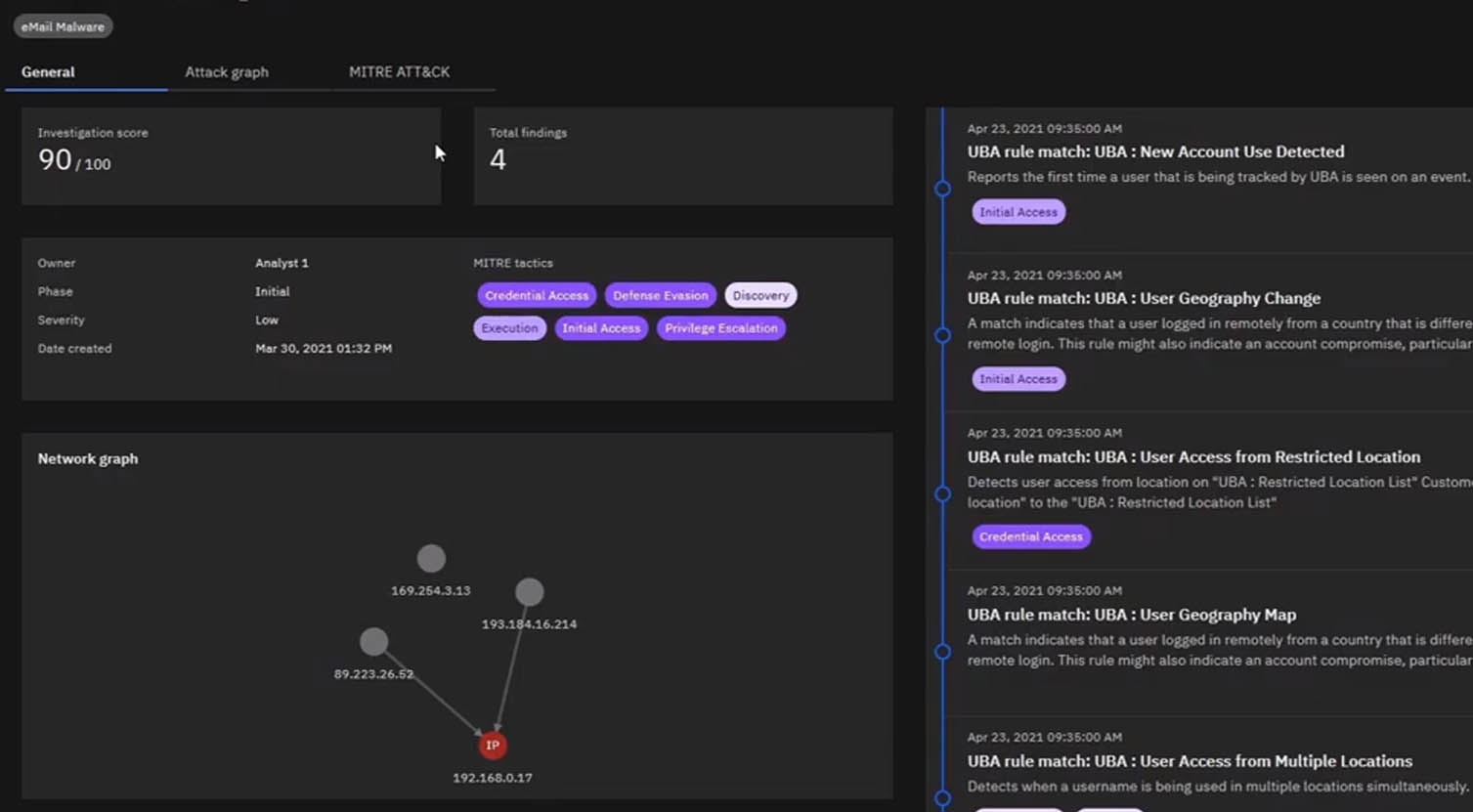
CCoE researchers are working on developing automatic security incident investigation and response capabilities for modern Security Operation Centers (SOCs). Incident investigation and determination of response consume excessive time and resources from the SOC analysts. Automating this process and providing the analyst with decision support mechanisms allows analysts to spend much less time on each incident, and makes it possible for the SOC team to better handle incidents, despite staff and skill shortages.
Our solution for automatic incident investigation includes several phases that pull data to support the decision making from different security systems such as SIEM, EDR, and others. This is done by correlating the alerts and data, then enriching the data with threat intelligence, asset information, risk, MITRE ATT&CK TTPs and more. The solution then presents analysts with information on the actions that should be done to mitigate the threat.
To accomplish this aggressive research agenda, we employ methods from graph theory, artificial intelligence, and data science. Our work involves understanding and experimenting with security products and platforms, and open source technologies such as STIX, Sigma, and MITRE ATT&CK.
A first version of this work was productized as the Threat Investigator application on IBM Cloud Pak For Security Version 1.6, and we continue to evolve and improve it. Watch the demo here.